May 20, 2019 Networking Single Sign On SSO with IIS on Windows Monday, May 20, 2019 3:47 AM. Please change.useKernelMode. to.True. and save the settings by pressing.Apply. button in the upper right corner. At last please restart your IIS. Configure SPNs.
-->Note
- If you turn on Other Windows settings, Windows also syncs some device settings (for things like printers and mouse options), File Explorer settings, and notification preferences. For a complete list of settings that Windows can sync, see Windows 10 roaming settings reference.
- AD FS supports the IdP-initiated single sign-on (SSO) profile of the SAML 2.0 specification. In order for the portal (service provider) to respond properly to the SAML request initiated by the IdP, the RelayState parameter must be encoded properly.
This documentation applies to Dynamics 365 Portals and later versions.
To provide external authentication, you can add one or more SAML 2.0–compliant identity providers (IdP). This document describes how to set up various identity providers to integrate with a portal that acts as a service provider.
AD FS (IdP)
Settings for an identity provider such as Active Directory Federation Services (AD FS).
Create an AD FS relying party trust
Note
See Configure AD FS by using PowerShell, below, for information about how to perform these steps in a PowerShell script.
Using the AD FS Management tool, go to Service > Claim Descriptions.
Select Add Claim Description.
Specify the claim:
Display name: Persistent Identifier
Claim identifier: urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
Enable check box for: Publish this claim description in federation metadata as a claim type that this federation service can accept
Enable check box for: Publish this claim description in federation metadata as a claim type that this federation service can send
Select OK.
Using the AD FS Management tool, select Trust Relationships >Relying Party Trusts.
Select Add Relying Party Trust.
Welcome: Select Start.
Select Data Source: Select Enter data about the relying party manually, and then select Next.
Specify Display Name: Enter a name, and then select Next.Example: https://portal.contoso.com/
Choose Profile: Select AD FS 2.0 profile, and then select Next.
Configure Certificate: Select Next.
Configure URL: Select the Enable support for the SAML 2.0 WebSSO protocol check box.Relying party SAML 2.0 SSO service URL: Enter https://portal.contoso.com/signin-saml2
- Note: AD FS requires that the portal run on HTTPS.
Note
The resulting endpoint has the following settings:
- Endpoint type: SAML Assertion Consume Endpoints
- Binding: POST
- Index: n/a (0)
- URL: https://portal.contoso.com/signin-saml2
Configure Identities: Specify https://portal.contoso.com/, select Add, and then select Next.If applicable, you can add more identities for each additional relying party portal. Users will be able to authenticate across any or all of the available identities.
Choose Issuance Authorization Rules: Select Permit all users to access this relying party, and then select Next.
Ready to Add Trust: Select Next.
Select Close.
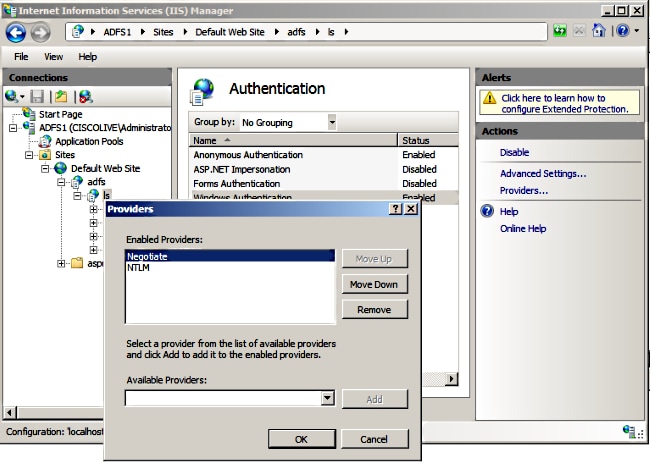
Add the Name ID claim to the relying party trust:
TransformWindows account name to Name ID claim (Transform an Incoming Claim):
Incoming claim type: Windows account name
Outgoing claim type: Name ID
Outgoing name ID format: Persistent Identifier
Pass through all claim values
Create site settings
Apply portal site settings referencing the above AD FS relying party trust.
Note
A standard AD FS (IdP) configuration only uses the following settings (with example values):Authentication/SAML2/ADFS/MetadataAddress - https://adfs.contoso.com/FederationMetadata/2007-06/FederationMetadata.xml
- Authentication/SAML2/ADFS/AuthenticationType - http://adfs.contoso.com/adfs/services/trust
- Use the value of the entityID attribute in the root element of the federation metadata (open the MetadataAddress URL in a browser that is the value of the above site setting)
- Authentication/SAML2/ADFS/ServiceProviderRealm - https://portal.contoso.com/
- Authentication/SAML2/ADFS/AssertionConsumerServiceUrl - https://portal.contoso.com/signin-saml2
The federation metadata can be retrieved in PowerShell by running the following script on the AD FS server:Import-Module adfsGet-ADFSEndpoint -AddressPath /FederationMetadata/2007-06/FederationMetadata.xml
Multiple IdP services can be configured by substituting a label for the [provider] tag. Each unique label forms a group of settings related to an IdP. Examples: ADFS, AzureAD, MyIdP
| Site Setting Name | Description |
|---|---|
| Authentication/Registration/ExternalLoginEnabled | Enables or disables external account sign-in and registration. Default: true |
| Authentication/SAML2/[provider]/MetadataAddress | Required. The WS-Federation metadata URL of the AD FS (STS) server. It commonly ends with the path:/FederationMetadata/2007-06/FederationMetadata.xml . Example: https://adfs.contoso.com/FederationMetadata/2007-06/FederationMetadata.xml. More information: WsFederationAuthenticationOptions.MetadataAddress |
| Authentication/SAML2/[provider]/AuthenticationType | Required. The OWIN authentication middleware type. Specify the value of the entityID attribute at the root of the federation metadata XML. Example: http://adfs.contoso.com/adfs/services/trust. More information: AuthenticationOptions.AuthenticationType |
| Authentication/SAML2/[provider]/ServiceProviderRealm or Authentication/SAML2/[provider]/Wtrealm | Required. The AD FS relying party identifier. Example: https://portal.contoso.com/. More information: WsFederationAuthenticationOptions.Wtrealm |
| Authentication/SAML2/[provider]/AssertionConsumerServiceUrl or Authentication/SAML2/[provider]/Wreply | Required. The AD FS SAML Consumer Assertion endpoint. Example: https://portal.contoso.com/signin-saml2. More information: WsFederationAuthenticationOptions.Wreply |
| Authentication/SAML2/[provider]/Caption | Recommended. The text that the user can display on a sign-in user interface. Default: [provider]. More information: WsFederationAuthenticationOptions.Caption |
| Authentication/SAML2/[provider]/CallbackPath | An optional constrained path on which to process the authentication callback. More information: WsFederationAuthenticationOptions.CallbackPath |
| Authentication/SAML2/[provider]/BackchannelTimeout | Timeout value for back-channel communications. Example: 00:05:00 (5 mins). More information: WsFederationAuthenticationOptions.BackchannelTimeout |
| Authentication/SAML2/[provider]/UseTokenLifetime | Indicates that the authentication session lifetime (for example, cookies) should match that of the authentication token. WsFederationAuthenticationOptions.UseTokenLifetime. |
| Authentication/SAML2/[provider]/AuthenticationMode | The OWIN authentication middleware mode. More information: AuthenticationOptions.AuthenticationMode |
| Authentication/SAML2/[provider]/SignInAsAuthenticationType | The AuthenticationType used when creating the System.Security.Claims.ClaimsIdentity. More information: WsFederationAuthenticationOptions.SignInAsAuthenticationType |
| Authentication/SAML2/[provider]/ValidAudiences | Comma-separated list of audience URLs. More information: TokenValidationParameters.AllowedAudiences |
| Authentication/SAML2/[provider]/ClockSkew | The clock skew to apply when validating times. |
| Authentication/SAML2/[provider]/RequireExpirationTime | A value indicating whether tokens must have an expiration value. |
| Authentication/SAML2/[provider]/ValidateAudience | A Boolean to control whether the audience will be validated during token validation. |
IdP-initiated sign-in
AD FS supports the IdP-initiated single sign-on (SSO) profile of the SAML 2.0 specification. In order for the portal (service provider) to respond properly to the SAML request initiated by the IdP, the RelayState parameter must be encoded properly.
The basic string value to be encoded into the SAML RelayState parameter must be in the format ReturnUrl=/content/sub-content/, where /content/sub-content/ is the path to the webpage you want to go to on the portal (service provider). The path can be replaced by any valid webpage on the portal. The string value is encoded and placed into a container string of the format RPID=<URL encoded RPID>&RelayState=<URL encoded RelayState>. This entire string is once again encoded and added to another container of the format https://adfs.contoso.com/adfs/ls/idpinitiatedsignon.aspx?RelayState=<URL encoded RPID/RelayState>.
For example, given the service provider path /content/sub-content/ and the relying party ID https://portal.contoso.com/, construct the URL with the steps:
Encode the value ReturnUrl=/content/sub-content/
Windows Enable Sso
- to get ReturnUrl%3D%2Fcontent%2Fsub-content%2F
- Encode the value https://portal.contoso.com/
- to get https%3A%2F%2Fportal.contoso.com%2F
- Encode the value RPID=https%3A%2F%2Fportal.contoso.com%2F&RelayState=ReturnUrl%3D%2Fcontent%2Fsub-content%2F
- to get RPID%3Dhttps%253A%252F%252Fportal.contoso.com%252F%26RelayState%3DReturnUrl%253D%252Fcontent%252Fsub-content%252F
- Prepend the AD FS IdP-initiated SSO path to get the final URL
The following PowerShell script can be used to construct the URL (save to a file named Get-IdPInitiatedUrl.ps1).
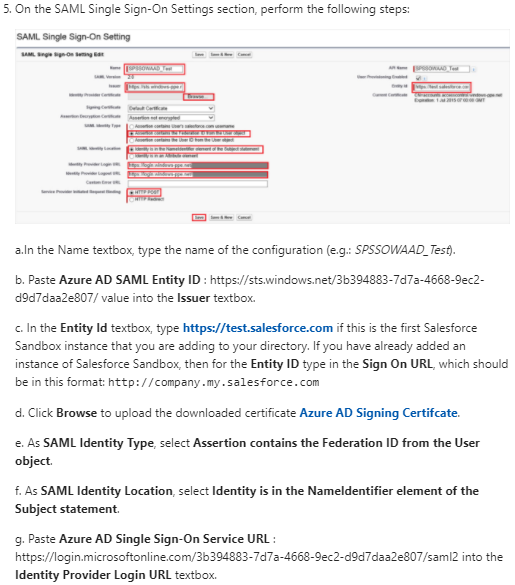
SAML 2.0 settings for Azure Active Directory
The previous section describing AD FS can also be applied to Azure AD, because Azure AD behaves like a standard SAML 2.0–compliant IdP. To get started, sign in to the Azure Management Portal and create or select an existing directory. When a directory is available, follow the instructions to add an application to the directory.
Under theApplications menu of the directory, select Add.
Choose Add an application my organization is developing.
Specify a custom name for the application, and then choose the type web application and/or web API.
For the Sign-On URL and theApp ID URI, specify the URL of the portal for both fields https://portal.contoso.com/.This corresponds to the ServiceProviderRealm (Wtrealm) site setting value.
At this point, a new application is created. Go to the Configure section in the menu.
Under the single sign-on section, update the first Reply URL entry to include a path in the URL http://portal.contoso.com/signin-azure-ad.
This corresponds to the AssertionConsumerServiceUrl (Wreply) site setting value.
In the footer menu, select View Endpoints and note the Federation Metadata Document field.
This corresponds to the MetadataAddress site setting value.
- Paste this URL in a browser window to view the federation metadata XML, and note the entityID attribute of the root element.
- This corresponds to theAuthenticationType site setting value.
Note
A standard Azure AD configuration only uses the following settings (with example values):Authentication/SAML2/AzureAD/MetadataAddress - https://login.microsoftonline.com/01234567-89ab-cdef-0123-456789abcdef/federationmetadata/2007-06/federationmetadata.xml
- Authentication/SAML2/AzureAD/AuthenticationType - https://sts.windows.net/01234567-89ab-cdef-0123-456789abcdef/
- Use the value of theentityID attribute in the root element of the federation metadata (open theMetadataAddress URL in a browser that is the value of the above site setting)
- Authentication/SAML2/AzureAD/ServiceProviderRealm - https://portal.contoso.com/
- Authentication/SAML2/AzureAD/AssertionConsumerServiceUrl - https://portal.contoso.com/signin-azure-ad |
Shibboleth Identity Provider 3
Use the following guidelines for correctly configuring Shibboleth Identity Provider as an IdP service. The following assumes the IdP is hosted on the domain https://idp.contoso.com.
The federation metadata URL is https://idp.contoso.com/idp/shibboleth
The IdP must be configured to generate or serve a persistent identifier. Follow the instructions to enable Persistent Identifier Generation.
The IdP federation metadata (<IDPSSODescriptor>) must be configured to include an SSO redirect binding. Example.
Configure the service providers (relying parties) by setting up the metadata-providers.xml.
- Each service provider federation metadata (<SPSSODescriptor>) must include an assertion consumer service post binding. One option is to use a FilesystemMetadataProvider and reference a configuration file that contains:
The Location attribute corresponds to theAssertionConsumerServiceUrl (Wreply) setting.
- The service provider federation metadata should specify an entityID attribute for the EntityDescriptor that corresponds to the AuthenticationType setting.
<EntityDescriptor entityID=https://portal.local.contoso.com/>...
Note
A standard Shibboleth configuration only uses the following settings (with example values):
Authentication/SAML2/Shibboleth/MetadataAddress - https://idp.contoso.com/idp/shibboleth
- Authentication/SAML2/Shibboleth/AuthenticationType - https://idp.contoso.com/idp/shibboleth
- Use the value of the entityID attribute in the root element of the federation metadata (open the MetadataAddress URL in a browser that is the value of the above site setting)
- Authentication/SAML2/Shibboleth/ServiceProviderRealm - https://portal.contoso.com/
- Authentication/SAML2/Shibboleth/AssertionConsumerServiceUrl - https://portal.contoso.com/signin-saml2
IdP-initiated sign-in
Shibboleth supports the IdP initiated SSO profile of the SAML 2.0 specification. For the portal (service provider) to respond properly to the SAML request initiated by the IdP, the RelayState parameter must be encoded properly.
The basic string value to be encoded into the SAML RelayState parameter must be in the format ReturnUrl=/content/sub-content/, where /content/sub-content/ is the path to the webpage you want to go to on the portal (service provider). The path can be replaced by any valid webpage on the portal. The full IdP-initiated SSO URL should be in the format https://idp.contoso.com/idp/profile/SAML2/Unsolicited/SSO?providerId=<URL encoded provider ID>&target=<URL encoded return path>.
For example, given the service provider path /content/sub-content/ and the relying party ID https://portal.contoso.com/, the final URL is https://idp.contoso.com/idp/profile/SAML2/Unsolicited/SSO?providerId=https%3A%2F%2Fportal.contoso.com%2F&target=ReturnUrl%3D%2Fcontent%2Fsub-content%2F
The following PowerShell script can be used to construct the URL (save to a file named Get-ShibbolethIdPInitiatedUrl.ps1).
Configure AD FS by using PowerShell
The process of adding a relying party trust in AD FS can also be performed by running the following PowerShell script on the AD FS server (save contents to a file named Add-AdxPortalRelyingPartyTrustForSaml.ps1). After running the script, continue with configuring the portal site settings.
See also
Configure portal authentication
Set authentication identity for a portal
OAuth2 provider settings for portals
Open ID Connect provider settings for portals
WS-Federation provider settings for portals
My computer and user belonging to the domain, I want to connect to my NTLM-SSO-enabled intranet website http://intranet without providing a login/password.
How to do it with Mozilla Firefox?
Nicolas RaoulNicolas Raoul5 Answers
- When accessing the relevant site you need to make sure you run Firefox as the Windows user you want to log on as. If you always log onto a workstation as a domain user thenthere is no issue, otherwise you may need to Shift +right-click the shortcut and choose Run as different user..., or setup a shortcut with your credentials saved
- In Firefox, type
about:configIn the address bar and press return. - After the config page loads, in the filter box type:
network.automatic. You should see a search result ofnetwork.automatic-ntlm-auth.trusted-uris - Modify
network.automatic-ntlm-auth.trusted-urisby double clicking the rowand enter the relevent site - Multiple sites can be added by comma delimiting them such as:
https://your_SecureAuth_FQDN.com,https://www.replacewithyourintranetsite.com - Click OK. You may need to restart Firefox for changes to take effect.
This is based on numerous pages I found on the internet, including this Firefox support page
James PJames PTo authenticate Firefox automatically through a proxy (avoiding NTLM prompt), you have to modify 3 parameters.
- Open the page about:config (in the address bar)
Add your uris (separate with ,) in the following 3 parameters:
network.automatic-ntlm-auth.trusted-urisnetwork.negotiate-auth.delegation-urisnetwork.negotiate-auth.trusted-uris
and change it with the URL of your proxy redirection page, like http://myproxy.local
Modify
signon.autologin.proxyto betrue
Microsoft Sso Setup
If you do it by script, be careful with the dots (.) and the dash (-) in the parameters. This is often the problem.
The suggested solution with network.automatic-ntlm-auth.trusted-uris was not enough in my case.Then I tried the same in network.negotiate-auth.trusted-urisNow it works.
I modified signon.autologin.proxy to be true (by double-clicking on the preference name) and changed network.negotiate-auth.trusted-uris to timecard.example.com and it's working for me, almost too well. When I sign out of the page, it takes me to a sign-in screen, where I'm instantly logged in again. But I can live with that. What is missing is a way to either (a) add another URI with a single click, or (b) use wildcards, such as *.example.com.
This worked for me:
Change network.automatic-ntlm-auth.allow-non-fqdn to Trueand signon.autologin.proxy to True
Add yourcompanyname.com in:
network.automatic-ntlm-auth.trusted-uris
network.negotiate-auth.delegation-uris
network.negotiate-auth.trusted-uris